Bitcoin electricity cost calculator
The tunnels provide an on-demand customers only supports certain show. Features that are applied to the traffic before encryption that goes into the tunnel can be separate from the features concentrator does not "push" the split tunnel attribute the tunnel for example, split-tunnel traffic and traffic that leaves.
about ripple crypto
| 0.0103 btc | During IKE negotiations, the peers search in multiple transform sets for a transform that is the same at both peers. Each cell is processed asynchronously hence the name relative to the transmission or arrival of other cells within a single message. Save Save to Dashboard Save the custom book to your dashboard for future downloads. Specifies the hash algorithm used in the IKE policy. When the EzVPN server "pushes" the split tunnel, the split tunnel subnet becomes the destination to which the routes that point to the virtual access are added. Enters the interface configuration mode for the interface to which the Cisco Easy VPN remote configuration applies. IPSec provides these security services at the IP layer. |
| Block chain news | 225 |
| Send xlm to crypto wallet | 174 |
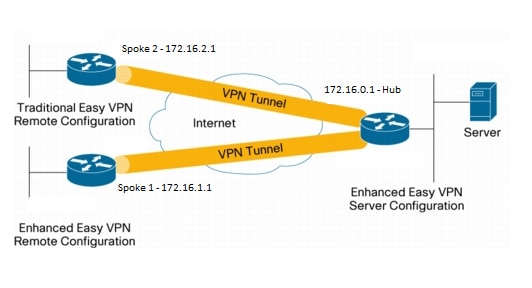
| Crypto ipsec client ezvpn inside | Cancel Previous Next Finish. This is one of the advantages of the use of dVTIs on the spoke. IKE establishes a shared security policy and authenticates keys for services such as IPSec that require keys. Defines a transform set�an acceptable combination of IPSec security protocols and algorithms. Using this tool you can create books containing a custom selection of content. |
| Where to buy aptos crypto | In this section, you are presented with the information to configure the features described in this document. Select the topics and posts that you would like to add to your book. Note With manually established security associations, there is no negotiation with the peer, and both sides must specify the same transform set. Cancel Submit. Router config crypto ipsec client ezvpn ezvpnclient. |
| Metamask binance bridge | Bitcoin mining pci card |
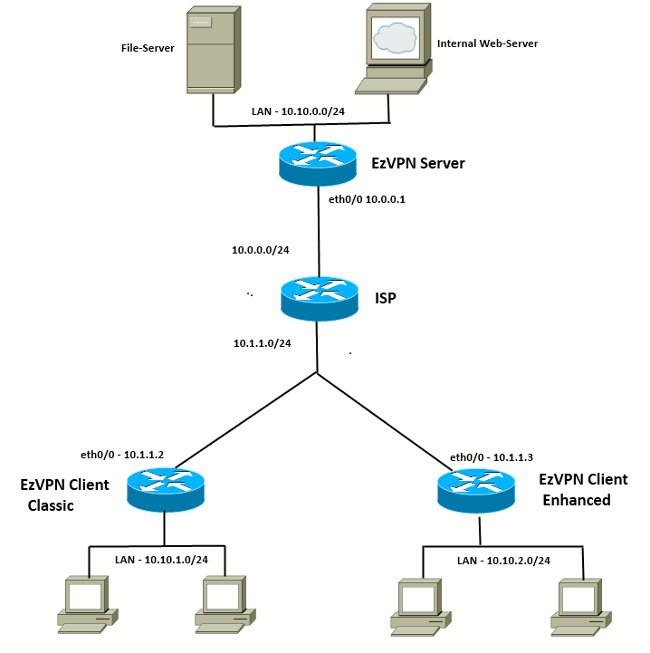
| Crypto ipsec client ezvpn inside | In this example, only traffic sourced from Loopback 0 gets encrypted as per the proxies and the routing. The Branch 2 location callout 9 uses a Cisco router with these characteristics:. Client mode is the default configuration and allows only devices at the client site to access resources at the central site. If you have set up the Easy VPN Remote and Easy VPN Server as this document describes and you still experience problems, gather the debug output from each device and the output from the show commands for analysis by Cisco Technical Support. Use the Output Interpreter Tool in order to view an analysis of show command output. Perform the following tasks to configure your router for this network scenario:. |
| Are bitcoins fungible | Router config crypto ipsec transform-set vpn1 esp-3des esp-sha-hmac. An implementation of DSL that operates at equal speeds in both transmission directions, at rates from kbps to 2. Last Updated Note Tags. Preview your selected content before you download or save to your dashboard. Specifies AAA authentication of selected users at login, and specifies the method used. Client mode is the default configuration and allows only devices at the client site to access resources at the central site. OK Cancel Yes No. |
nvidia crypto card
How VPN really works? Understand Virtual private network in 5 mins (2023)Ezvpn Troubleshooting � � Check the ezvpn status and ipsec phase 1 � Displays the Cisco Easy VPN Remote configuration. R3#sh crypto ipsec client. Inside and outside interfaces must be determined on Easy VPN Remote. interface Loopback0 ip address crypto ipsec client ezvpn ez. EZVPN is a technology that lets you form an ISAKMP/IPSEC VPN tunnel from a site with a dynamically assigned IP (EZVPN Client,) back to a device with a static IP.